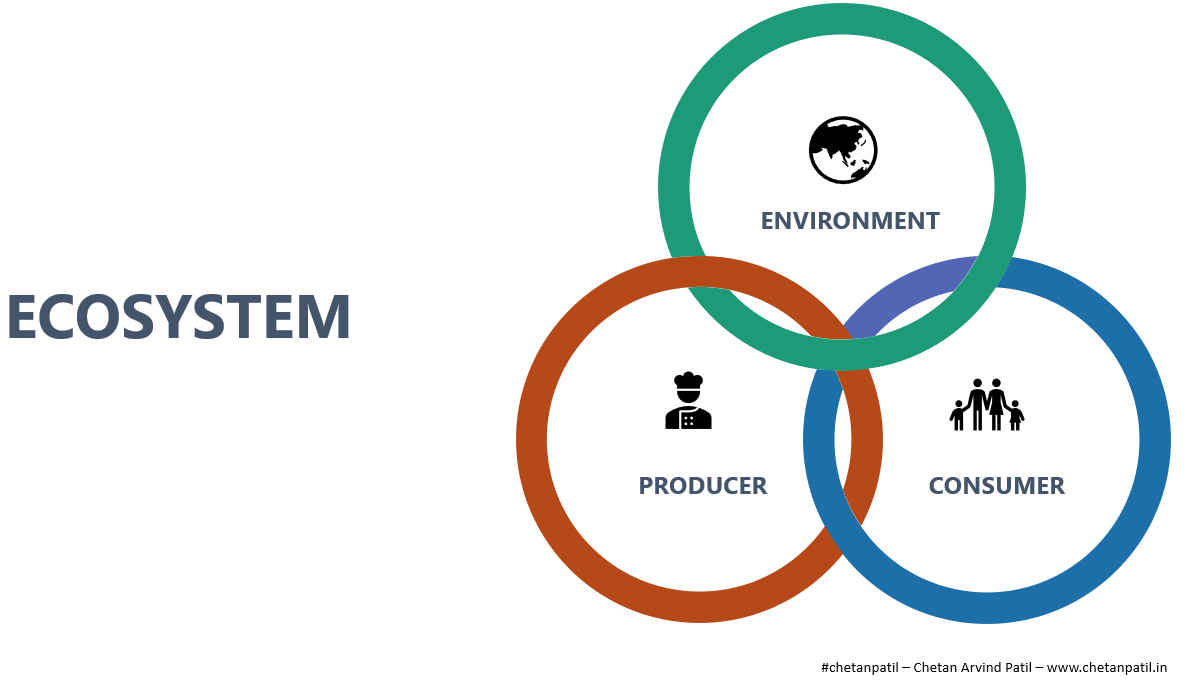
An ecosystem requires synchronized interaction of a Producer, Environment, and a Consumer. The inter-dependency and synchronous working leads to a perfect ecosystem on which life survives.
In the last few decades, the definition of the ecosystem has been applied to the technology world. Ecosystem development in different business segments has enabled innovations, which has in turn provided the world with new products and solutions.
In technology, an ecosystem is majorly reliant on the software and hardware systems. Due to the increased proliferation of internet users worldwide, the ecosystem has moved to the digital domain too.
All the ecosystems in software, hardware, and digital domain have created different platforms for anyone with the right skills to develop elegant solutions. The connected world allows anyone to take advantage of the existing infrastructure to provide products and services directly to the intended consumer.
However, the development of ecosystems has been limited to each of these three domains only and it is vital to understand how future modern platforms will look like.
HARDWARE PLATFORMS
The invention and innovation of transistors in the last half-century made possible the development of several unique hardware solutions that have taken computing to every corner of the world.
The form factors of computing devices have changed a lot in the last two to three decades, largely due to the Moore’s law. Every year the world gets to witness incredibly compact and insanely fast computer systems.
The computers that were only supposed to be part of the research centers in the form of mainframe and servers, transformed into the smaller form factor of desktops in the 1980s and 1990s.
The desktop allowed everyone to have their personal computers (PCs) at homes and offices. These PCs are capable of performing fast calculations, running high resolution videos and games apart from having ability to run applications that allow completion of numerous tasks in the shortest possible time.
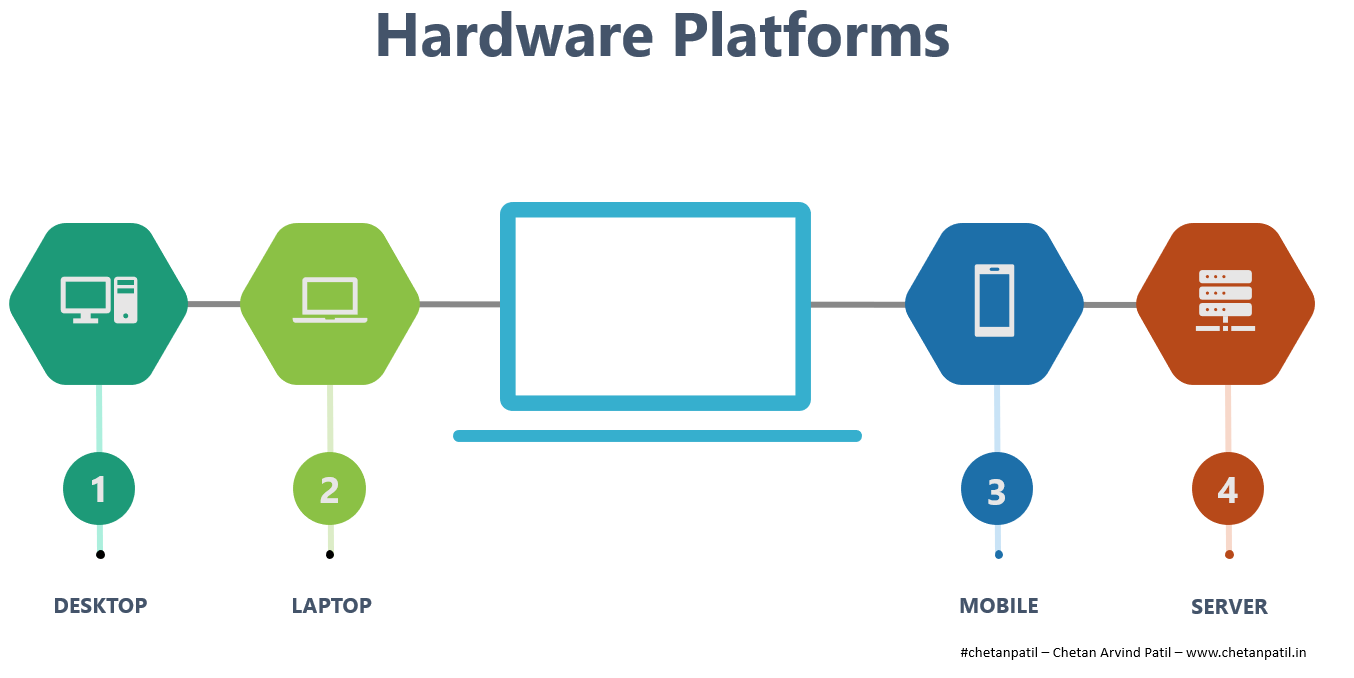
In the late 1990s and early 2000s, portable laptops took over the world. Companies started innovating with advancement processors and graphics, and so were able to deliver content on the go. Businesses also became more mobile.
Right after laptops, smartphones were launched in the early 2000s which allowed on the go connectivity. Smartphones connected the world at the click of a button. The form factor and battery life made it very easy to capture and consume information in real time.
All these hardware devices have lead to the creation of hardware platforms that allow anyone to be connected and perform task remotely. The ecosystem of hardware platforms ensures that one can deploy ideas, software, and applications for consumers to use from anywhere on any hardware of their choice.
The amazing innovative work being done by semiconductors, manufacturing, and assembly companies around the world is also the major reason for the existence of hardware platforms for everyone.
With the improvement in connectivity, these hardware platforms have become the most critical part of the life. All the smart devices, computers, servers, sensors, and internet routers together drive hardware platforms, that are enabling innovation like never before.
SOFTWARE PLATFORMS
In parallel to the invention of hardware (transistors and electronics chips), one more innovative work was getting developed. It started with different types of programming languages and then moved to graphical user interface (GUI). A combination of both gave birth to the advanced softwares.
Software took advantage of the computing capability of the hardware to provide solutions that allowed completion of tasks in hours, which otherwise would take days. Later on, with the introduction of operating systems, the hardware started to become more intuitive and smart.
UNIX, LINUX, and Microsoft Windows played key role in ensuring that developers can contribute by deploying applications written for hardware systems.
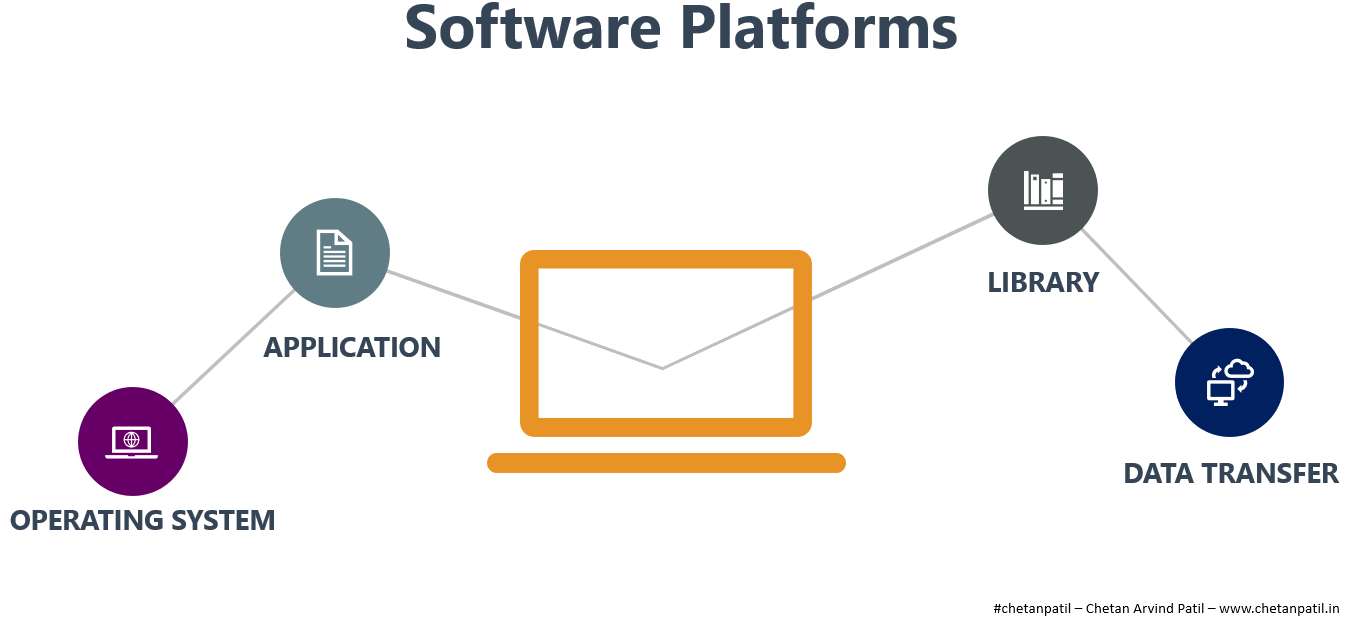
Software innovation has also allowed access to the hardware internals with the help of drivers written using different libraries. With the synchronized working of the operating systems, libraries, and applications on top of a hardware platform enabled data transfer.
In the pre-internet era, data transfer was largely limited to a floppy disk, hard drive, and a pen drive. However, post-internet era has been all about data packet transfer from one hardware to another with the help of secure software platforms.
Software, which started a journey on mainframes as punch cards, now could run on the smallest possible hardware and sensors with minimal power consumption. This has lead to the creation of software platforms that allow the world to be digitally connected and is more real-time than ever.
DIGITAL PLATFORMS
Hardware and software have been in existence for many years. The last 40 years saw numerous innovations, form factors, and the true potential of these two computer systems. The computer solutions built with hardware and software combination helped building a nexus between people by providing enormous life-enriching smart solutions.
Today, with the internet becoming part of everyone’s life, the opportunities for the next few decades are infinite. Already, modern services in 2020 are more data-driven which ensure that the right product is available at the right time for the right user.
The combination of hardware, software, data, and the internet has provided a new platform to the world, called digital platforms.
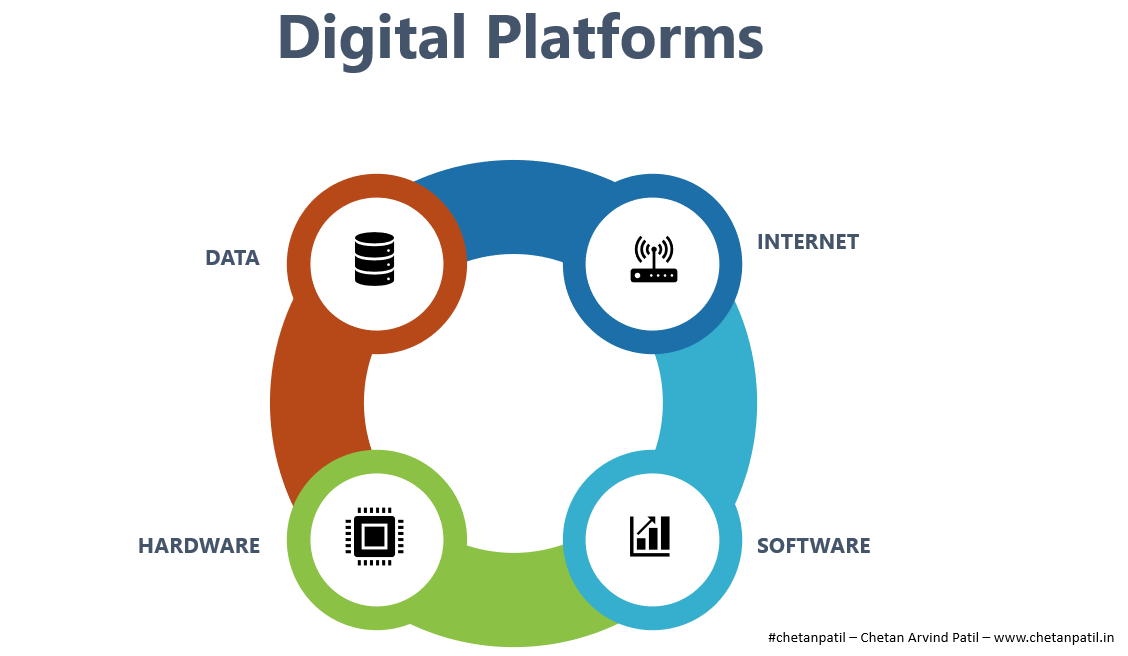
Digital platforms are built on top of the hardware and software, but it differs from hardware and software platforms due to the additional use of data and the internet to provide over the top product and services. With the help of the internet, products and services can be optimized and delivered remotely.
The data points generated with the increased usage of the internet allows any business to adapt to the consumer’s needs by accessing demand based on data points from different consumer behavior.
As the world moves towards more advanced wireless solutions, the innovative solutions on top of the digital platforms are only going to increase.
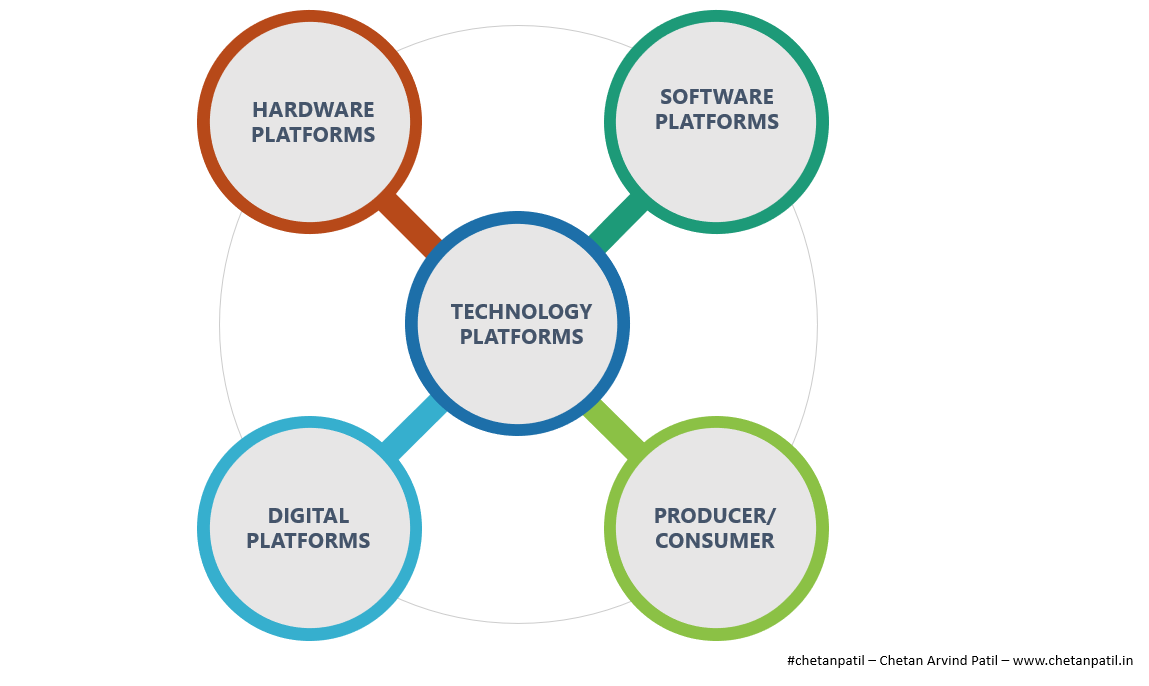
TECHNOLOGY PLATFORMS
In computer programming, the concept of Application Programming Interface (API) is so powerful that it gets overwhelming to realize the elegance of solutions it helps to implement.
In short, API allows access to the services with the help of the software commands. For example, consider the payment gateway on an eCommerce website using a third party payment solution to process payments. With the help of API, the consumers can pay using different payment modes while the eCommerce website need not be worried about the processing and security of the payment details, as it relies on the secure API from by the third party.
Similarly, there are other solutions in the market that are API driven.
The technology platform applied using API will play a crucial part in realizing the one world market,
Technology platforms are a combination of hardware, software, and digital platforms with the added element of a producer and a consumer. It is an open platform that has consumers on board with producers who have become capable of selling products without investing capital in the underlying technology.
Technology platforms also allow single or combination of other platforms to exists and thrive. The creators of the technology platforms themselves will not be able to make full use of it until and unless the platform itself is open to both the producer and consumer.
One of the major drawbacks of technology platforms will be the amount of time and capital expenditure it will take to create. Not every company will be able to develop the technology platforms, and thus their number will be limited.
It is fair to say that the technology platforms were already in the making for the last few decades. Today, these platforms are more relevant than ever. Mobile networks is one example of such platforms that allow hardware to digital platforms creation.
It will be exciting to see how the next decade with the proliferation of high-speed wireless networks will drive the technology platform innovation.



