Photo by Proxyclick Visitor Management System on Unsplash
Identity is the backbone of Know Your Customer (KYC) process. Every country and company has its process and technology to ensure that the correct people have access to the correct resources. In the digital world, the Know Your Customer is moving to Electronic Know Your Customer (eKYC).
Today, the world still relies on different types of identity documents for different services, with each service generating its identity numbers. From driving license to passport the list to have unique identity numbers and identity documents to prove the authentic identity of the owner never ends.
On top of this, the majority of the countries have national identification programs that capture demographic or/and bio-metric information and connect it to an unique identification number. For example, the United States of America has Social Security Number, and then India has Aadhaar.
Such national identification programs have met with a lot of criticism, but the fact is that the digital world will eventually rely on these centralized systems to shift from the traditional approach to have a separate identity document and identification number which used to prove the ownership.
There is a dire need to move away from this process of providing a unique identity to each of the service types so that not only the process is centralized and relies on unique identification number and management but is also fast, secure, and enables cost-saving.
The unique identification number and management solutions are important and critical in the digital world, and demands advanced solutions like Electronic ID (eID).
IDENTITY PROBLEM
To implement and use unique identification numbers and management, connected and secured infrastructure is required to ensure that the identity of the person and entity is preserved without compromising on security.
Even though these unique identification programs have been implemented and in use, some gaps are there which still exist.
Authentication on a connected system after producing identity card details is still not secure, costly, unreliable, and a slow process. Another fact is that all this requires an investment in infrastructure that validates the identity and makes the system costly for the business authenticating the details. Eventually, all these charges are passed to the consumer which makes it a costly process in the long term.
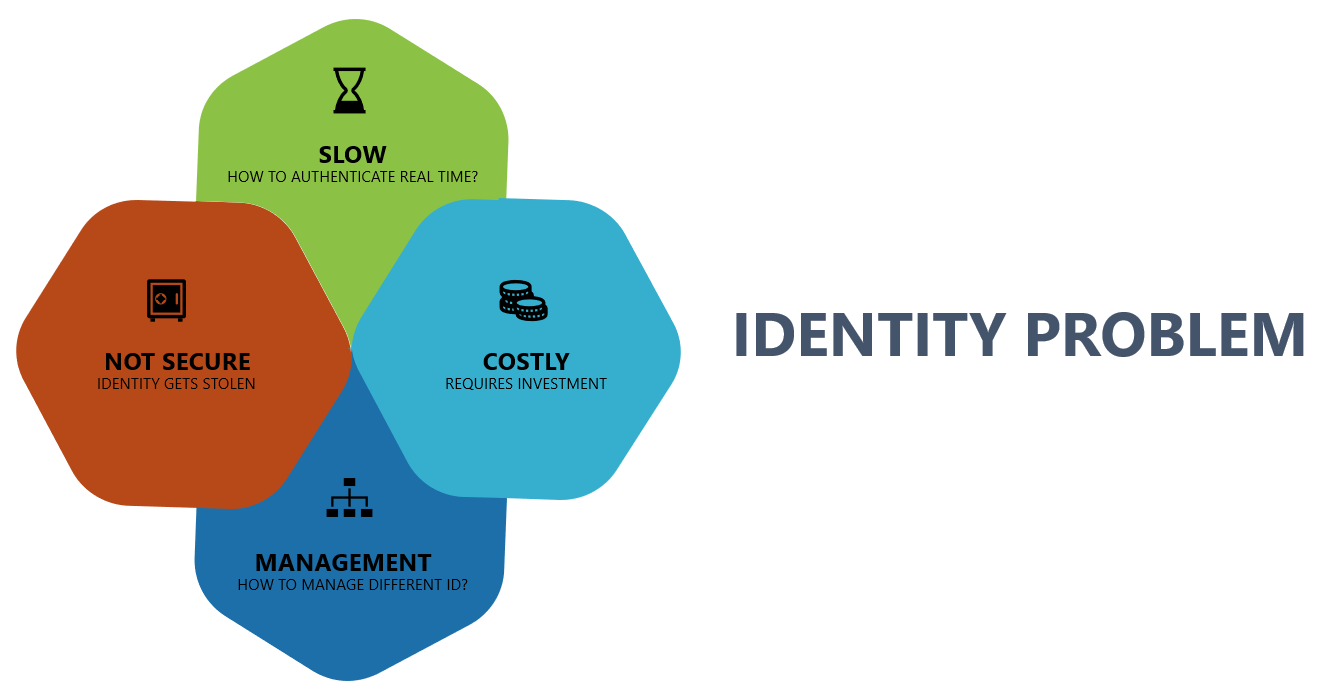
Data management is another issue because lack of standardization leads to add on investment in order to upgrade the systems to accept the new unique identification features while ensuring backward-compatibility.
After all these investments and infrastructure to authenticate, there is no guarantee that the system is secure. With all the advanced approaches, the identity still gets stolen and thus invites fraud.
All these issues make a strong case for unique identification number and management but using Electronic Identity (eID).
IDENTITY SOLUTION
One of the most talked-about solutions to solve identity management crises is Electronic ID (eID), which makes use of sensors and NFC enabled Electronic Identification Card (eIC) to authenticate the identity of the people.
eID relies on demographic or/and bio-metric information to validate correct details. These details are already part of many national identification programs. By making use of eID, these programs can solve the identity crisis by ensuring security and centralization by data storage.

The smart cards that use eIDs are called eICs which are equipped with electronic chips to ensure that the data is stored securely and also transferred with encryption when required. Along with these features, these eICs also make use of the Trusted Platform Module (TPM) that enhances security and avoids theft.
There are already many solutions in the market catering to the need for eICs. Like NXP’s National Electronic ID (NeID) solution not only secures the information but also allows high return on investment. A similar solution is also available from Infineon that is also targeted toward NeID.
With EU going for Electronic IDentification, Authentication, And Trust Services (eIDAS), the adoption of eICs is going to be faster than anticipated.
IDENTITY INNOVATION
Many innovative solutions around eICs are already available. Countries have already started to make use of eICs in their national identification program where the true potential of eICs is.
For example, Estonian Identity Card program is one of the earliest programs to make use of eICs to register its citizen. This innovation allows easy access to various public services and also secures the identity of the users.
The VideoID, SmileID, and SignatureID solutions created by eID is another example of how to make the most of the technology to allow faster onboarding of customers by ensuring that the information provided is accurate and is not falsified.
IDENTITY FUTURE
Given how both software and hardware is taking over the world, it is certain that the future of identity is the body. Technology is going to make Microchip Implant a day to day activity. Certainly, this is going to be voluntary.
It will be interesting to see the development and adoption of eICs. Given the digital world in the future, eICs will certainly take over traditional identity cards. The question is how soon.
Many advanced eID based technological solutions will come out of innovative startups around the world. Creating businesses and solutions on top of the eIDs and eICs will also open up new market.
With Work From Anywhere, the identity authentication is also going to be from anywhere with the help of Electronic ID (eID).





